The large number of malicious code files that exist on the Internet may be the main reason for us to adopt these tips and practical guides that we will mention in this article, which have no other objective than that of make Windows security prevail for our best working comfort.
Considering that there are different routes of contagion of which we could be being victims at a certain moment, the fullfilment of security requirements of our operating system has to be one of the main aspects to take into account.
1. Improve Security with a good Antivirus
When referring to a good antivirusWe are necessarily trying to mention that it should be paid; a free tool implies certain limitations, same that could be allowing the entry of a file of malicious code to our computer.
Viruses, Trojans, malware, Spyware, and a few other malicious code files not only come from different Internet environments, but also, they may be integrating into some plugins within our Internet browser, environment that free applications generally cannot detect.
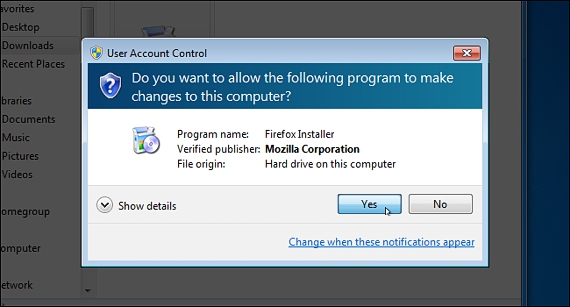
2. Let the UAC be always on
The UAC (User Account Control) is generally always activated, although certain tools and applications ask the user to temporarily deactivate this function; the situation usually occurs when trying to install some kind of application in which you want to register an illegal serial number.
From Windows 7 onwards, this UAC will always be activated by default, a function that aims to prevent infection of the operating system by malicious software (a crack).
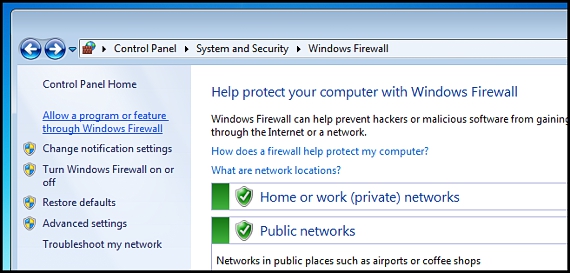
3. Always configure and enable the Firewall
This is another aspect of fullfilment of security requirements that we must always take into account, environment that never in life should we deactivate it since with this, we would be allowing the entry of any type of threat to Windows.
From Windows XP onwards the Windows Firewall is activated by default; If there is a tool that we are sure does not contain any type of malicious code, then we can configure this Firewall to allow a direct connection between our team with their respective servers.
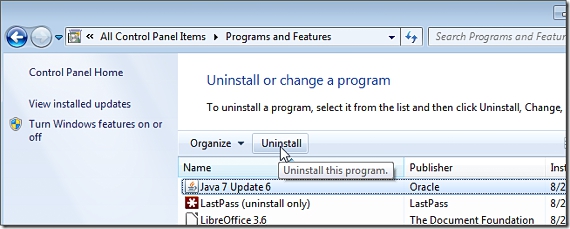
4. Disable Java
Java is one of the tools that is generally used to visit certain websites; unfortunately, if a user does not find the latest version of this add-on, they could be the victim of some kind of malicious code file.
Java has suffered a large number of attacks due to its immense vulnerabilities, holes that are used by hackers who try to collect information through different Internet cookies. It is recommended to uninstall Java from Windows, although if it is really required, the application that requests it will reinstall it.
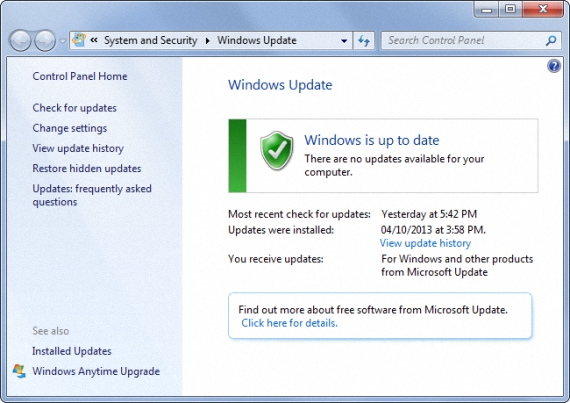
5. Keep the system updated with Windows Update
Despite the failures that could occur with certain Windows updates, it is always recommended that they be carried out in our operating system.
This is because new patches are suggested by Microsoft, which are intended to lock to some holes Security; Many of these patches are dedicated to correcting bugs that generally appear in different Internet browsers or in certain third-party applications.
6. Install safe applications in Windows
A lot of people have been trying to download and install applications obtained from torrent, which generally tend to have certain threats in their respective cracks.
For this reason, the download of applications has to be done only from official sites and not from some dubious ones.
7. Avoid installing pirated software
This aspect is intrinsically linked to what we mentioned in the previous term; pirated software will never bring good working results to our personal computer.
If at a certain moment our computer is working perfectly well and then starts to get slower and slowerPerhaps we should analyze since when did this situation occur; with certainty that you can conclude like us when mentioning that, This failure occurred when we installed some kind of pirated software.
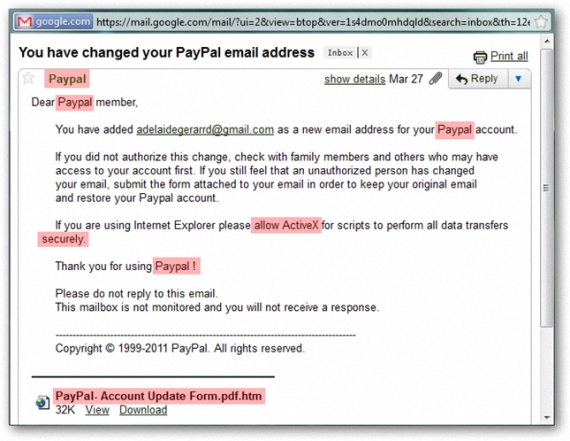
8. Be careful with social engineering
Despite the fact that this aspect was perfectly well identified some time ago, new Windows users often fall into the trap of social engineering.
It refers to false messages that reach our email, where we are asked for the access credentials to the service or any other environment, it under the "threat" that our account will be closed or definitely interrupt, which is a lie.
9. Frequently change passwords
Another security aspect that we must take into account is in the access passwords to our Internet services.
If at a certain point we have suspected that someone entered our email (or any other similar environment), perhaps already we have changed the password for a new one; Never in our life should we reuse that password that was previously hacked, since it is found in the database of these unscrupulous users.
10. Use strong passwords
This is the main recommendation that is usually given to users who browse different Internet environments; the use of strong passwords can help us to keep the information we have in different places in the cloud and on our computer well protected.
A strong password is generated by the combination of alpha numeric (letters and numbers), uppercase, lowercase and certain characters that make it more difficult to be deciphered.
More information - Download ESET Smart Security 5, Vuze Torrent Downloader: Download Torrent Files on Android, How you can disable applications that start with Windows, The Importance of Generating Strong Passwords