If you leave your computer only for a moment, you will never be able to know if someone has entered to review the information stored on it, through the file explorer. It does not matter if the hard drives do not have something compromising, but rather, that the files that are part of an important project could be housed there.
This becomes the main reason why we should adopt all kinds of measures to lock both mouse and keyboard from our Windows computer; If we succeed, we could leave the team completely only knowing that absolutely no one will have the possibility to enter to review what we have saved on the hard drive, something that we could achieve with a few tools that we will mention below.
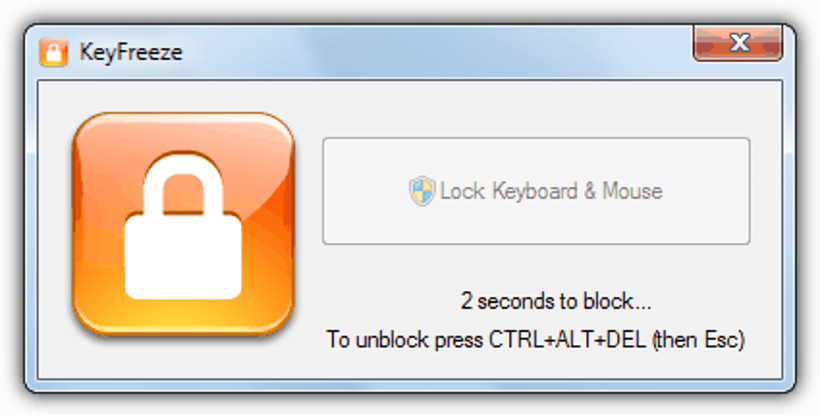
- 1. Keyfire
This is one of the easiest and simplest tools to use, which you can download and install completely for free in Windows.
When you have met that first requirement, you just have to run it by double-clicking on the respective icon of its shortcut. In that instant you will admire a small window with a countdown counter (five seconds) that when reaching the end, it will lock the functions of both the mouse and the keyboard. To go back to working on the computer, all you have to do is use the key combination CTRL + ALT + DEL and then press the ESC key, at which point we will be on the Windows desktop again. Here you will not find more options or the possibility of entering a password to enter Windows.
- 2. Toddler Trap
This could be considered the most anecdotal tool in the world, because after we download it and run it, we will only admire a small floating window that will appear in front of everything the content that is present at that moment on the Windows desktop.
If you leave the computer with this protection, anyone can come to admire the windows of the applications with which you were working, although they will not be able to do anything at all because they will all be blocked. Now, the developer of this tool mentions that to the small floating window (like the previous screenshot) that you have to locate in a strategic place so that no one can see it, because if someone clicks on the small "X" it will automatically close this window and therefore the computer can be used by anyone.
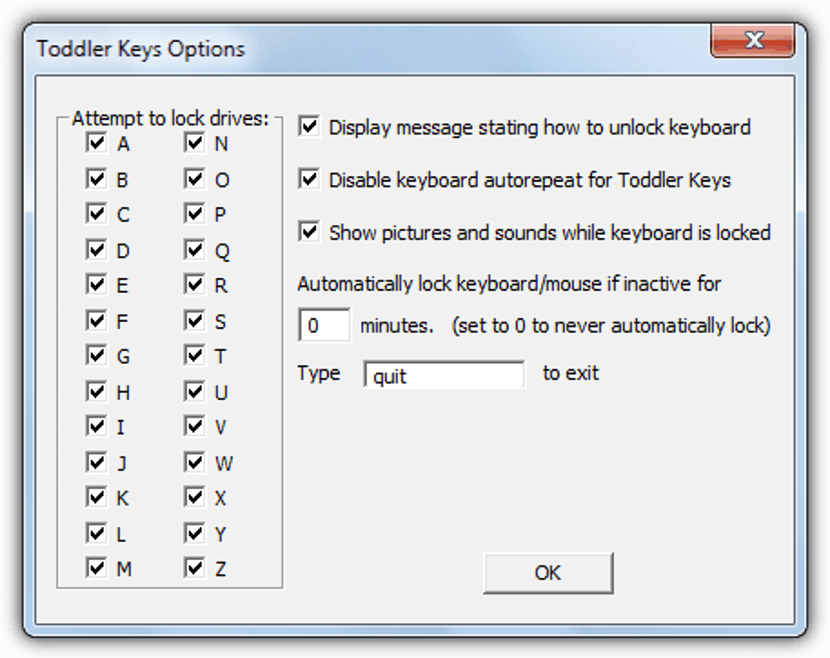
- 3. Toddler keys
This tool is a bit more complete than the ones we mentioned above. In addition to helping us to block the functions of both the keyboard and the mouse, it also has the possibility of preventing the operation of the tray of our CD-ROM drive, access to hard drives and even, locks the power button.
With this last function that we have mentioned, nobody would be able to turn off the computer by pressing this button.
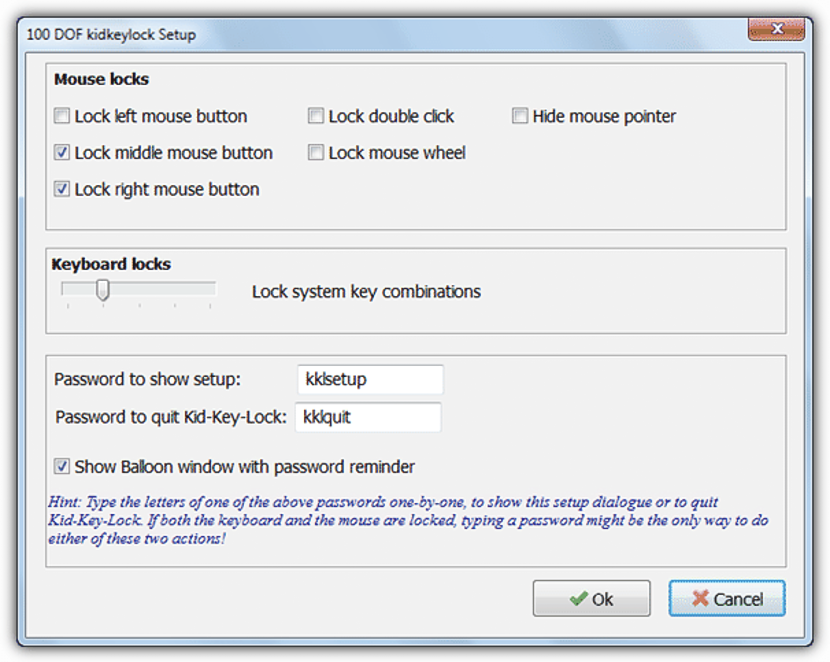
- 4. Kid-Key-Lock
For those who do not want to block all keyboard and mouse functions, this tool may be the solution. With it we will define if we want the actions resulting from pressing the left, right or the middle of our mouse to be blocked.
Besides that, you can also get ablock some keyboard functions and leave a few others free that we will surely use at any time. Unlike the tools we mentioned above, here there is the possibility of defining a password to render the application ineffective.
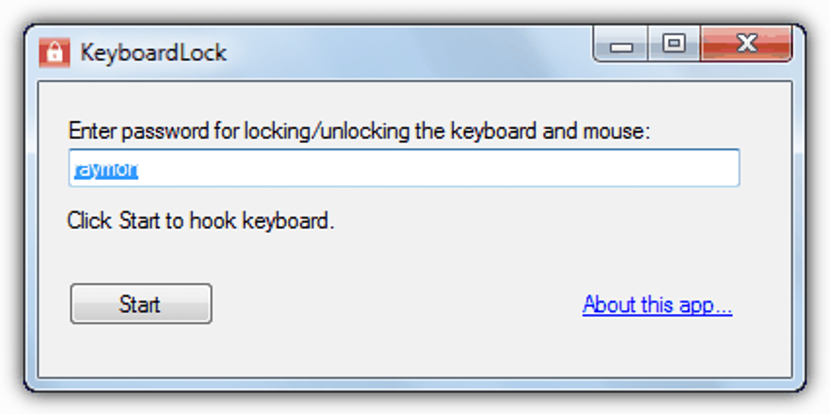
- 5.KeyboardLock
We could even mention that this tool has a very great similarity with the one we suggested at the beginning.
This is due to the fact that this tool also has the possibility of lock keyboard and mouse functions, counting on a minimalist interface where we only have to define the password to be able to render this tool ineffective.
We already have five alternatives that we could use at any time that we leave only the personal computer with Windows, which will help us primarily, to safeguard information on hard drives and that perhaps, is very important for any type of work and projects that we are doing at that moment.