
macOS, formerly known as OS X, the Mac operating system, has always been characterized, at least in theory, as one of the safest in the computer ecosystem, with Windows being the one that has always presented the greatest problems. But it is not entirely true, since macOS, like Windows and the different variants of Linux, They all have security holes.
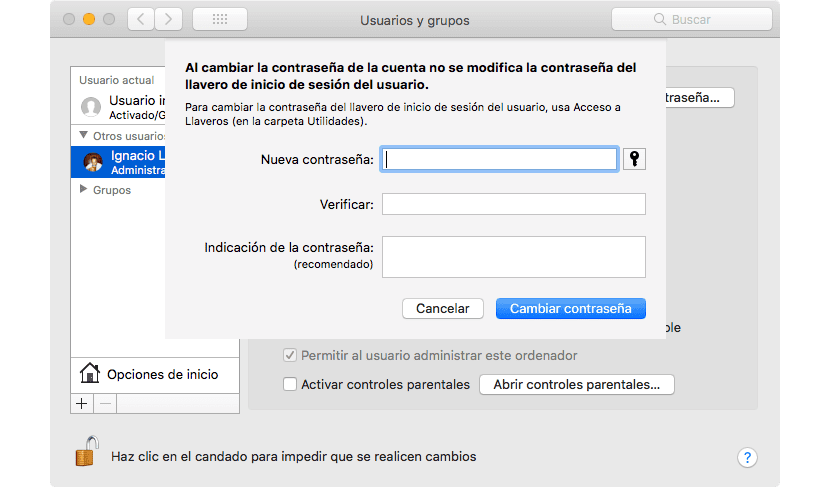
The latest one that has been discovered and which poses a very significant risk to the data stored inside it, affects Macs that are running the latest version of macOS High Sierra. This vulnerability allows us to access the administrator mode from a guest account, an account that generally it does not usually have a password, hence its name. Once we have accessed, we can change the administrator password without having to know it at any time, since it directly shows us the window to change the administrator password, as we can see in the image above.
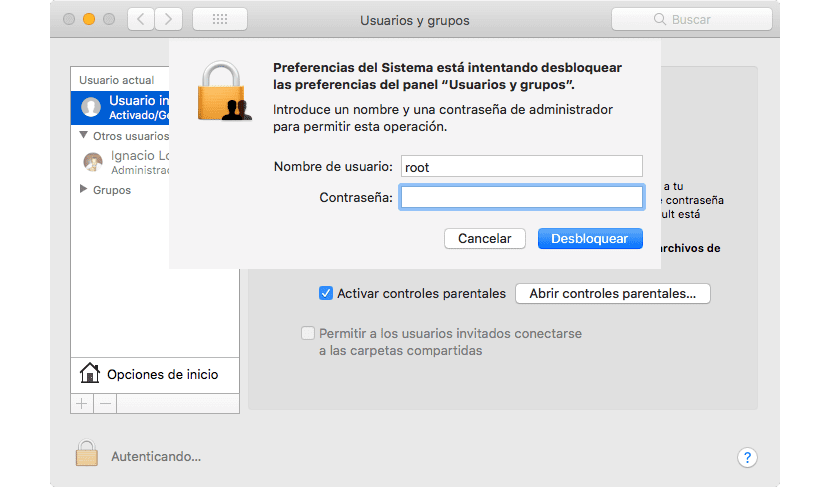
To be able to do this, we just have to access from the System Preferences of our user account, click on the padlock located in the lower left corner. Next we write the word "root" as the username and press the enter key several times until you accept it. Once this process is completed, we have the administrator controls of the Mac that we are using at our disposal.
Fix this macOS security issue
The solution is first to disable the guest user, a process that we can do through System Preferences as detailed below.
- Within System Preferences we go to Users and Groups.
- Within Users and Groups, Select Guest User.
- Now, we deactivate the option Pallow guests to connect to this computer.
But to be completely sure and that new bugs of this type could put the security of the information that we store on our computer at risk, we must change the root password, which by default is associated with the "root" user. To do this, we will proceed as follows:
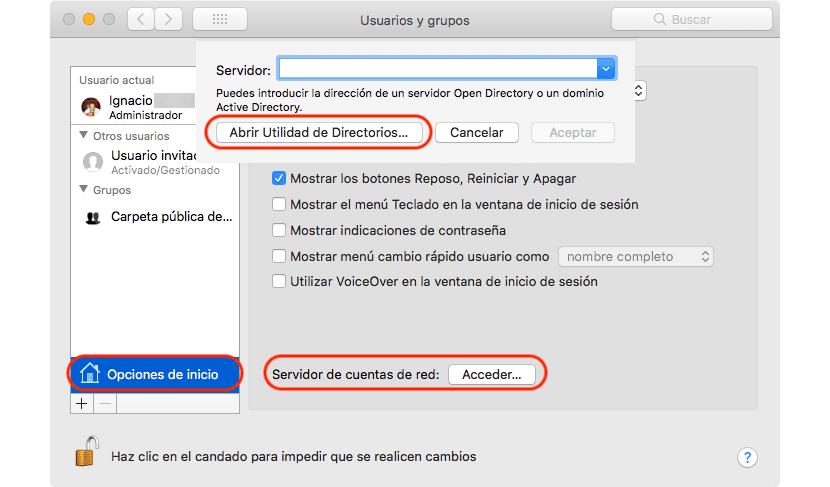
- We will head up to System preferences.
- Click on Users and Groups and select Ostartup options.
- Then click on Network account server, and press Open Directory Utility.
- In the next step, we go to the Edit menu and select Cchange Root user password.