Many people have come across great inconveniences when browsing a specific news item or website, something that becomes very annoying if we think that there is the correct information for our work and research.
Although there are a few tools that can help us (such as add-ons or extensions) to navigate through specialized sites of streaming television using Google Chrome, the need to try to research information on other websites can extend to different web pages that are possibly blocked. In this article we will mention a few alternatives that you can easily adopt when trying to navigate these web pages and also the possibility of taking care of privacy in this navigation.
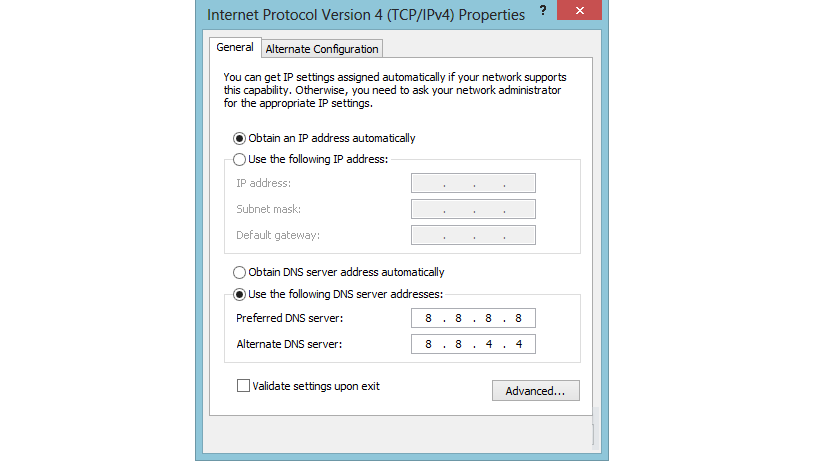
1. Define our DNS server settings
This is a practical but temporary solution, the same one that is usually offered by the different operators of those who administer the Internet service you are using. To do this, you would only have to enter the configuration or properties area of the network that you are using to connect to the Internet, and change from an automatic configuration (regarding the DNS server) to a different one.
This can be a bit conflicting if we do not know this information, although your service provider could offer you this information when it knows the problem you are having when entering a specific page; Although it is true that this could somehow solve the problem of navigating to a web page, the information will not yet have the privacy that you may want to use.
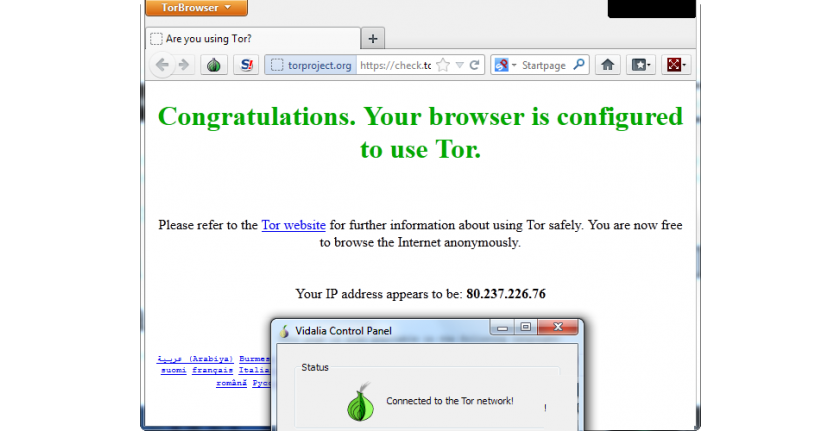
2. Browsing anonymously with TOR
TOR is an excellent alternative that we could use to browse the Internet anonymously, being the favorite of many users who want to review information from blocked websites without their activity being detected. Despite being a great advantage, this can involve great slowness in the display of pages.
The reason for this is due to the fact that TOR reaches these web pages using computer "tunnels", something that is reflected in a considerably large weight when trying to reach a specific website.
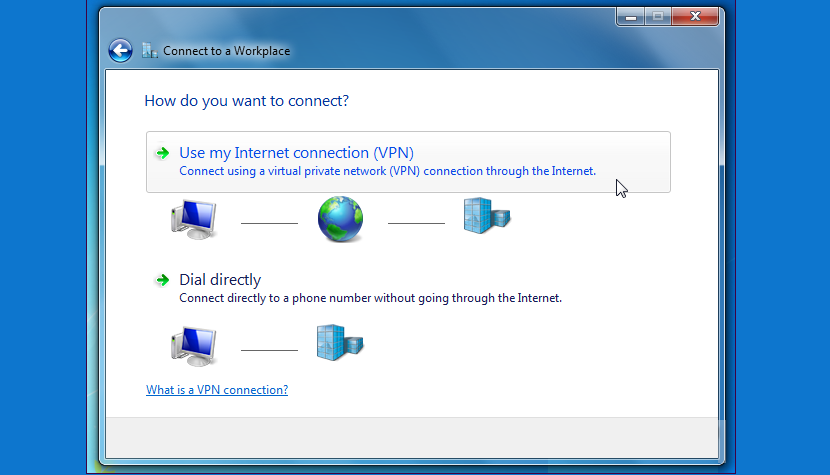
3. Connect to the Internet with a Virtual Private Network
There are a large number of tools that we could use for this purpose, most of which are completely free. Those who have developed the different applications to be able to connect to a virtual private network (VPN) mention that all the traffic generated is hosted on the servers of the investigated site.
Despite being a good alternative, this does not mean that all the information that is generated from our computer is completely private, because for this you would have to use some kind of method to encrypt to the same. An additional advantage offered by this type of mechanism is when working groups wish to connect from different regions of the planet, who will be the only ones who will have the possibility to admire the shared information.
4. Use an Encrypted Virtual Private Network
If you are interested in implementing the method that we suggest above, but encrypting your data about the traffic that is generated with this procedure, then you should try to hire one of the many services that exist on the web for that purpose. Unfortunately, that is the way in which many people can encrypt a virtual private network.
Now, those who consider themselves computer experts could use an interesting tool from Windows to create a tunnel type SSH with high encryption, having to follow the instructions proposed by the tool PuTTY.
Someone might believe that these alternatives could only be used by paranoid people, a situation further from reality, since there are currently many governments that are using a large number of filters so that the information issued from their respective regions cannot reach other different. Since a while ago the British government is already encouraging Internet providers (ISPs) to adopt this measure, being a matter of time for what is known as the SOPA law to be applied in different places, being a great lock with which we will have to battle very soon.