The information that we carry on our USB pendrive can be of great importance, this being the main reason why we should carry out this activity. Considering that every day these accessories are getting smaller and in them, the storage capacity is much larger, so encrypting the information on the USB flash drive is practically an urgent need that we should do at any time because most people tend to lose them on the way to use.
The only thing we need to be able encrypt the information of the USB pendrive is to know how to use all the means that we have available in our hands; so for example, the USB pendrive, our computer (in our case with Windows 7 or Windows 8) and of course, a free USB port to connect to this little accessory. As we can admire, each and every one of the elements that we have mentioned are available to be used at any moment.
Steps to encrypt the information on the USB flash drive
The process can take some time if our accessory has a lot of storage, so patience has to be one of the extra items to get through. Under no pretext should we remove our USB pendrive from the respective port while the process is running. In this first part we will teach the right way to power encrypt the information USB pendrive through a series of sequential steps:
- First we start our operating system (Windows 7 or Windows 8).
- Now we click on the button Start Menu.
- In the search space we write BitLocker.
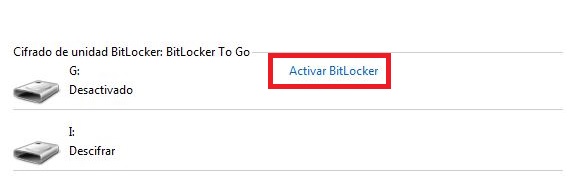
- From the results we choose the option «Bitlocker drive encryption«.
- We insert our USB pendrive into a free port on the computer.
- The new device will appear in the list.
- Choose the option «Enable BitLocker»Located towards the right side of the USB pendrive.
- Put a password that we remember in the next window that appears.
- Back up the password we have generated in a file.
- Initialize the process to encrypt the information of the USB pendrive.
With these simple steps that we have mentioned, it is only a matter of time for the encryption process of the information that is contained in our USB stick to be completed, which will depend on the amount of information as well as the storage space of this little accessory.
Disable the action of encrypting the information on the USB flash drive
Every time we insert our USB pendrive into a specific port on any computer, the information on it cannot be opened because the accessory is encrypted; to be able to review the content we will only have to enter the password that we generated in the previous step. Anyway, if you no longer want to have your USB pendrive encrypted, then you should only follow the following steps after having opened the encryption window with Bitlocker:
- We insert our USB pendrive.
- We search the list for our blocked USB stick (usually with a lock icon).
- We click on the button that says «disable BitLocker«.
- Write the password that we generated previously in the space of the new window.
These are the only steps we should follow so that our USB pendrive appears again in a normal state, that is, without being blocked as we had previously left it; despite the fact that we have done the procedure for a USB pendrive, the same procedure can be done for internal hard drives (secondary) as well as external, although the reader must be warned that this type of storage device can involve a long process, due to the large space that they can have.
If for any reason the user forgot the password that was used to encrypt the information USB pendrive, then you will have to use the file that was generated in one of the steps of the first part; If this option is used to unlock the USB pendrive, then the plain text document will have to be opened to be able to check inside, the key that BitLocker generated.
More information - Encrypt folders in Windows 7