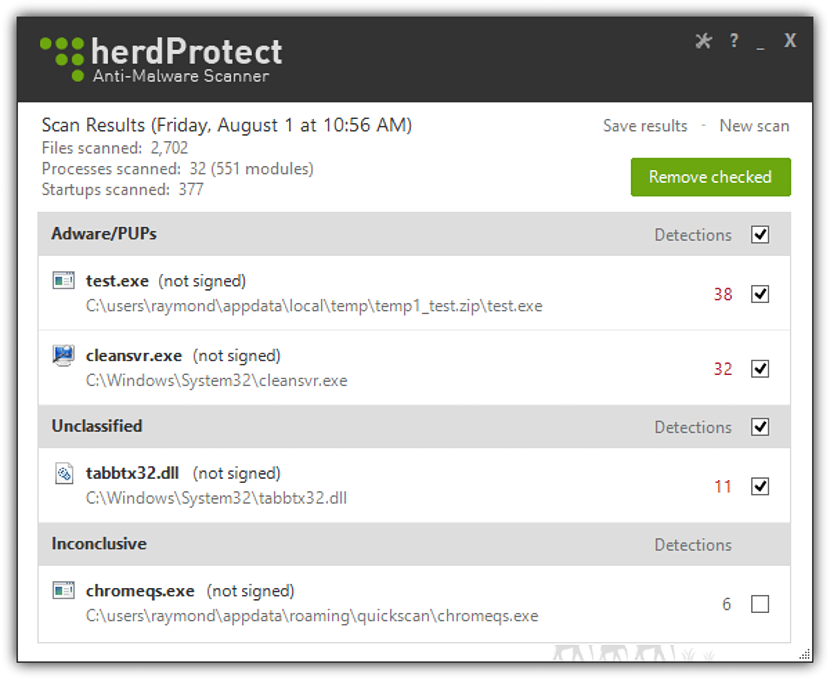
Is your Windows computer really protected? Even though we have followed the advice we gave earlier about the ESET installation as antivirus default in Windows, this does not mean that this security tool is infallible to certain threats that use a security hole.
The question could even be posed to anyone if despite having a good antivirus system installed on the computer, we still continue to feel certain number of discomforts in terms of effectiveness operating system workstation. If we have noticed a somewhat strange behavior then perhaps it is time to install HeadProtect, a tool that offers to search for the presence of some type of malware in Windows.
HeadProtect compatibility with Windows
HeadProtect is compatible with most versions of Windows, which is why there should not be any kind of problem in its operation with the different revisions proposed by Microsoft. The compatibility in fact we must analyze from the point of view of the antivirus that we have installed on our personal computer.
According to the HeadProtect developer, their tool does not cause any type of instability or incompatibility with any antivirus system that we have installed in Windows. This means that HeadProtect acts as an additional support to what the antivirus offers. Now, the way this security tool works is something very interesting to analyze, which we will mention below.
How to use HeadProtect to detect malware
You must first go to HeadProtect official website, where you will find two different versions to download. From our part we recommend you to buy the "laptop" because with this, you will not need to install it in Windows since even you could be using the USB pendrive.
The effectiveness of the results shown by HeadProtect is primarily based on the fact that this tool is supported by approximately 70 motors different that are specialized in this type of threats. The interface that we have placed in the upper part is the one with which you could come across; For many people it could be something completely incredible that a file of just 2 MB in size, has the possibility of performing such an exhaustive analysis when detecting malware. This situation is justified if we consider that the executable only acts as a small client that will connect to the different Internet servers and search engines that will provide information about what may be happening on our personal computer.
Additional settings and features in HeadProtect
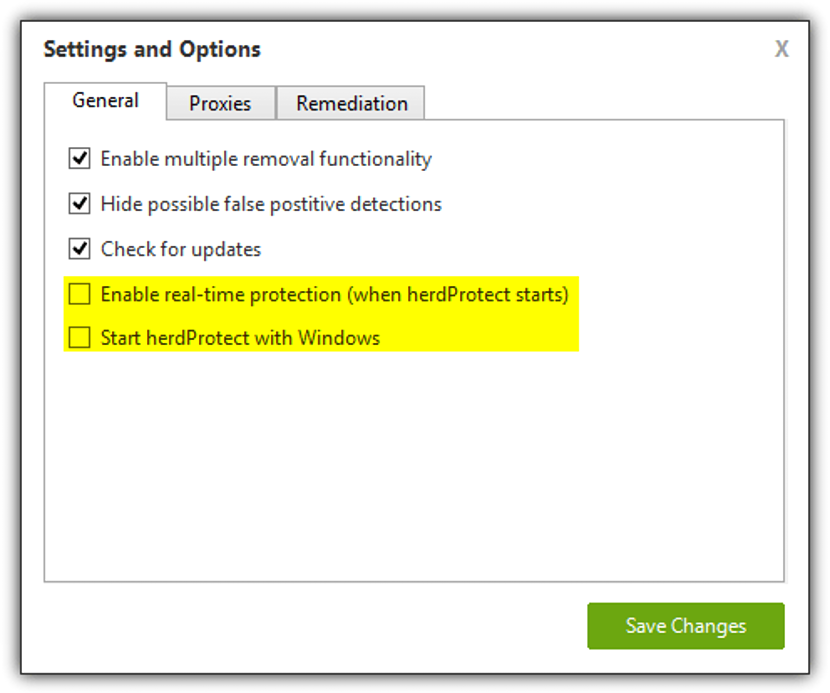
It does not matter if you download the portable version or the one that has to be installed in Windows, because in any of these versions you will have the possibility to enter its configuration to order HeadProtect to act, the way you want it.
For example, among these additional features that we could find in the HeadProtect configuration are those that will allow us:
- Hide or hide the "false positives" of malware
- Maintain an active review of database and application updates.
- Start "protection" mode in real time every time HeadProtect is run
- Order HeadProtect to start together with our Windows operating system.
We have placed at the top a screenshot of these additional features; The last two are highlighted right there, which could be necessary or unnecessary for a specific use. For example, if we are with the idea and fear that some malware has embedded itself in our operating systemIt would be well worth having the options that are highlighted with yellow in the proposed capture activated. If we are sure that a malware has not infiltrated Windows, then we could have these boxes deactivated and only run the application when we want to perform an operating system analysis.