When we have an Android mobile device (a tablet or a mobile phone) and no one else uses it, it may not be necessary to have to manage the applications and settings of the equipment, since no one else will try to enter an environment where only we know how use it perfectly well.
But what about if we give this tablet to a 10-year-old child; many things could happen at that moment, one of the most damaging for everyone, the one who navigates violent or age inappropriate apps in an accidental way. It is at that moment when we should think about using a tool that helps us block certain features of an Android mobile device, something that we will dedicate ourselves to doing in this article with the help of a security application.
A 4-digit pin to protect our Android device
The application that we are about to recommend at this moment is «Avast Mobile Security & Antivirus«, Same that you can get it completely free and lock 2 functions of your Android mobile device, something that is enough if we use this free in an intelligent way, although there is always the possibility of acquiring the paid version to be able to block more applications and functions on the computer. So that you have a slight idea of what you could be blocking after having acquired this tool, we will suggest what its developers have mentioned about it:
- Block access to the Google play store. With this, we are not only blocking the installation of some applications that the child could be accidentally choosing, but also the purchase of some of them if we have configured our credit card to this store.
- Lock system settings. It is also a great necessity, since the minor could be manipulating the storage space of our mobile device, something that could be harmful to us.
- Protect our installed applications. By protecting our equipment we will prevent a minor or any other person from uninstalling our favorite applications on the terminal.
We have mentioned the 3 most important reasons to take into account when protecting our Android mobile device with "Avast Mobile Security & Antivirus", and it must be the end user who defines the most important reasons for using the tool. Once we have downloaded and installed "Avast Mobile Security & Antivirus" we will only have to run it; at that very moment we will find a screen very similar to the one we will place below.
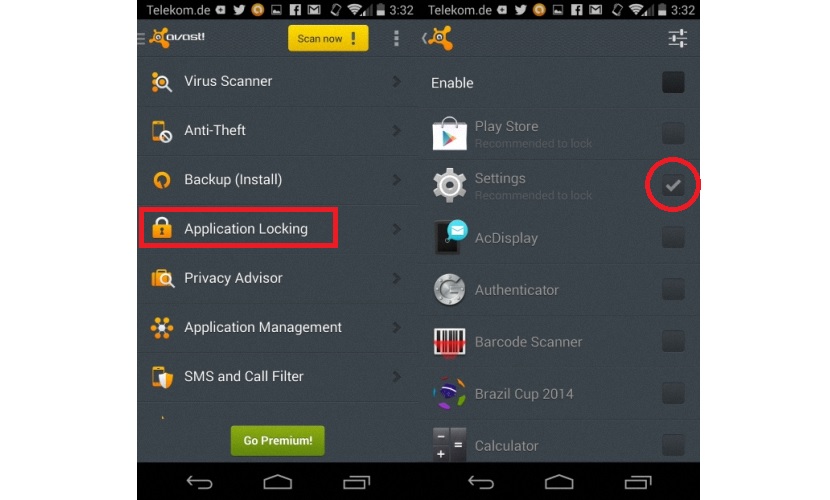
As you can admire, on the left side there are a few security options that this application offers us, having to choose for the moment the one that says «Application Locking; iImmediately, the list of all the applications and functions that our operating system and the terminal consist of will appear, only having to check each box to protect them. Remember that the free application will only allow us to block 2 of all these features, and it may be a good idea to choose:
- The Google Play Store.
- The configuration of our Android operating system.
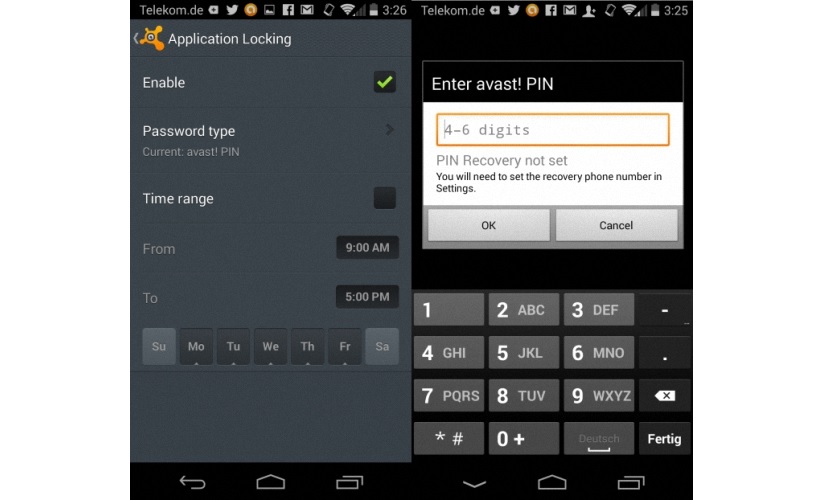
We shall define a 4-digit security key as an additional protection measure. When we hand over the terminal to a different person who wishes to enter these 2 environments that we have previously blocked as a suggestion, a small window will immediately appear in which the user will be asked to enter the 4 digits of the password that we have programmed previously.
As long as this password is not entered, any type of application or function that we have protected through this system will be unlocked.
Now, the tool offers us a few additional features within the security configuration, due to the fact that the end user can define, through a small calendar, the days and the time interval (from a specific time to a different time) in which this protection measure will be applied. Undoubtedly, this is a very important function to take advantage of, since if children use our terminal on the weekend (or at night), we should simply program it so that the unlock key is requested at those times.