
As smartphones and tablets have been invading the market, computers are being replaced by this type of device to make practically any query on the internet, thanks to the immediacy offered by having it always at hand. Currently on the market we can find a large number of devices of all prices.
Obviously the most expensive terminals, above all those of Apple and Samsung are usually the most desired by friends of others and the heart does not always skip when we do not know where we have left them or worse, if it has been stolen from us. Fortunately, we have different tools to easily find our device if we have lost it or it has been stolen.
If the terminal has been stolen, things get complicated since chances of recovery decrease, not only because it is very dangerous to try to recover it on our own, but because it is likely that the friends of others who have taken it, have turned it off to avoid locating the terminal.
For a couple of years, most manufacturers have offered us not only the possibility of locating our device and making it ring, ideal for when we cannot find it at home, in the car, at our workplace ... but also allow us to lock the device to become a brick and that it cannot be used again unless it is returned to the rightful owner.
How to protect my smartphone?

Protecting our smartphone with our fingerprint has become commonplace, thanks to the fact that more and more manufacturers are adding this technology. Thanks to this security measure, no person other than us you can access the terminal in no time, neither to invade our privacy nor to delete the account to which it is associated.
If our smartphone does not have this technology, we must use a pattern to unlock the terminal or use an unlock code to prevent access to anyone other than us. In this way, as with the fingerprint, we prevent that the account to which the terminal is associated can be deleted at least in Android terminals, since in iOS it is necessary to know the password of the Apple ID yes or yes to be able to completely unlink a terminal to an account and that it can be used with another, which is called iCloud Lock
Ways to locate our smartphone
Calling by phone
Although it may seem absurd, the traditional method is the one that always works, as long as the call volume of the device is not too low, as it will not allow us to hear it, especially if it has crept across the sofa or we have left it under a pile of clothes.
Location services
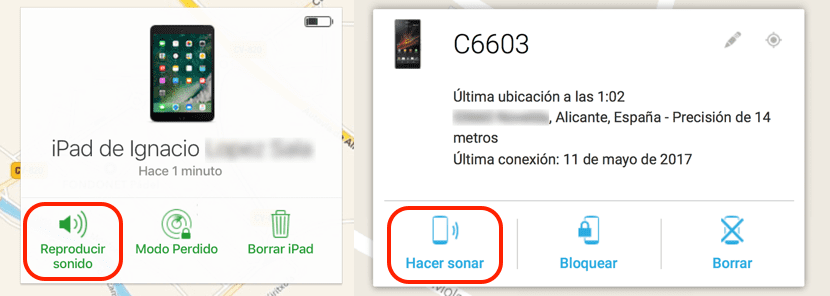
Both the Android Device Manager and Apple iCloud.com allow us to know at all times where our terminals are. Logically, if we have lost it at home or in another place where we are, showing us the location is irrelevant, although at least it confirms that it has not been stolen from us. Both services In addition to blocking and deleting all the content stored in the terminal, it also allows the device to emit a sound, quite sharp indeed, to be able to locate it quickly. This function is ideal, for when we are looking for our tablet, which we cannot call by phone or if our smartphone is silent or vibrating and through a phone call we cannot find out where the hell we have left it.
What to do if my mobile has been stolen?
Unless you personally know the person who stole your phone, which might allow some chance of getting it back talking to him or directly reporting him to the police, in these cases, the first thing we have to do is block our device so that you can not use it at any time.
How to block an iPhone if it has been stolen
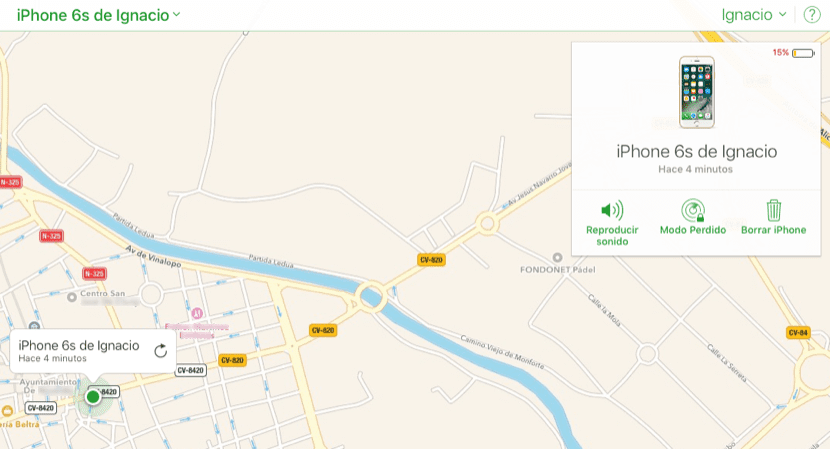
Apple offers us the possibility of being able to block our device through the iCloud.com website or through the Find my iPhone application, which we can have installed on any other device, be it iPad or iPod touch. Thanks to iCloud we can know at all times where is our device, including devices that do not have a mobile data connection, since by default this function enables the location of the same to be sent before running out of battery.
Once we have accessed iCloud.com we must go to Search, where all the devices that are linked to the same ID will appear. Then we just have to go to All devices and select the device we want to block. A window will appear on the map showing the last location of the device and the time that has elapsed since it was located. At the bottom will appear the options Play sound, Lost Mode and Erase iPhone.
Lost Mode locks the terminal giving us the option to display a message on the screen with a phone number in case someone finds it and wants to return it to us. In these cases, the phone cannot be unlocked to access it, since we cannot leave the screen that shows us that message. If we finally recover the terminal, we can unlock it to continue using it normally.
If the terminal does not have an internet connection at that timeAs soon as you connect to a mobile or data network, it will automatically be blocked. The Delete iPhone option allows us to delete all the data from that device along with the settings, but once the content is deleted we will not be able to locate it again through iCloud.
How to block an Android smartphone if it has been stolen
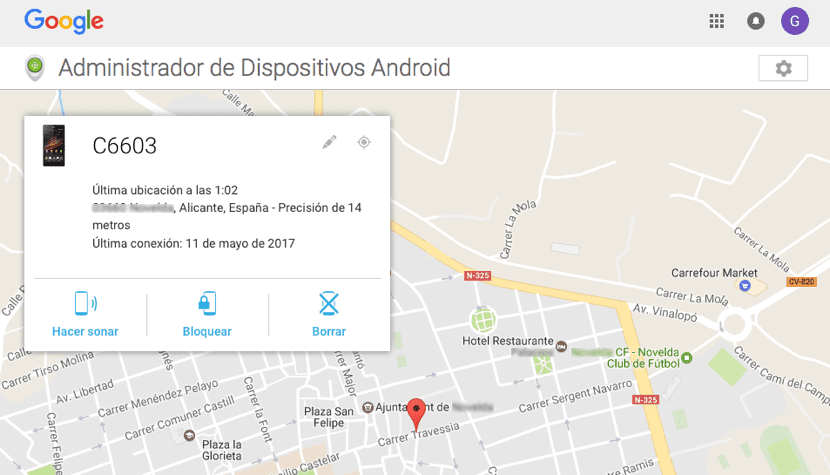
Like Apple, some manufacturers have also implemented measures of this type, but taking into account that all terminals are under the same Android umbrella, we are only going to explain the method that Google offers us to block the device. First of all we must go to the next page, a website that allows us to access the same options that Apple offers us for its iOS ecosystem.
A map will then be shown with the location of the terminal at that moment or the last known location of the terminal when it accessed the internet. Also, as with Apple's iCloud, the following options will be displayed: Ring, Lock, and Delete. These last two allow us to block the device immediately so that no one else can use it and erase all the content and the device settings respectively. If we select this last option, we will no longer be able to locate the terminal.
This news has helped me protect my mobile from any theft.
Thank you very much for the news