How many times do you check your bank account on the computer? If you carry out this task in a personal one, you may not have to worry so much, although there is always the possibility that you have installed some software with Keyloggers included.
The situation can be really worrying if you use rental computers, that is, those that are in the cyber, because here there is no guarantee that someone has manipulated them to capture the most access credentials towards different electronic stores and worse still, to bank accounts. For this reason, in this article we will suggest practical examples, tips and tricks you can use to avoid that the Keyloggers detect your activity in front of the keyboard.
1. Use a virtual keyboard in Windows
Obviously the first tip and trick that we will mention at this moment will be that, that is, that if we are using a computer that is not ours and we have some doubt about what may be installed there, we should disable the "virtual keyboard in Windows". The way to do it is something very simple to do, since you will only need:
- Click on the Windows Start Menu Button.
- In the search space write «keyboard«.
- From the results choose the option «on-screen keyboard«.
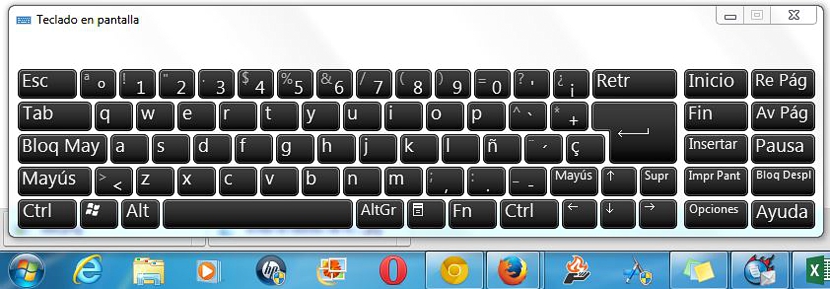
With these three simple steps that we have suggested, we will immediately have the Windows virtual keyboard in front of our eyes; the trick is to activate this tool only the moment we are going to write our access credentials to somewhere on the web. This "virtual keyboard" is present in most versions of Windows, so you can activate it at any time without having to download third-party applications.
When you are going to perform this operation, you just have to open the Internet browser and go to the web where you will have to put the respective credentials. After you have activated the virtual keyboard in Windows, you must place the cursor pointer in the space where the user name with the access password will be written and then start to press the virtual keyboard keys with your mouse pointer. If you want the protection not to break at any time, you should not press the keys with your fingers at any time.
2. Using Zemana AntiLogger in free version
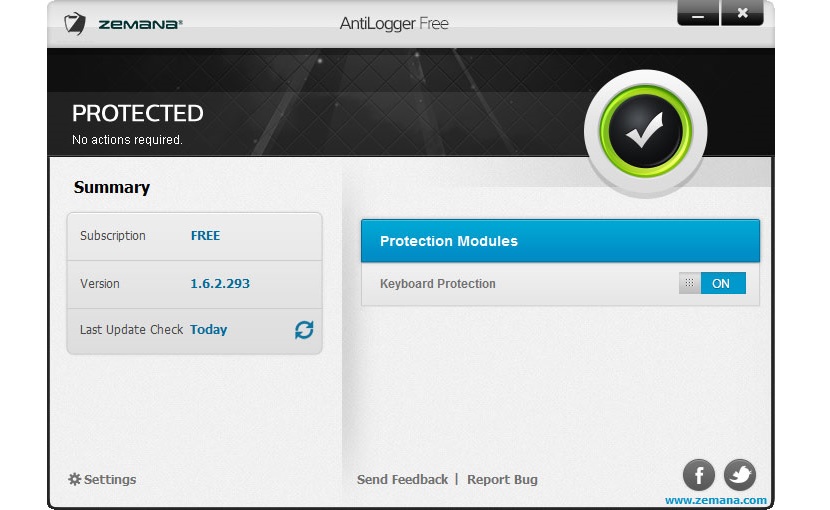
The method we suggested above may be too classic or primitive for many people, due to how annoying it would be to have to press each of the keys on this "virtual keyboard" with the mouse pointer. For this reason, another additional recommendation is found in an application named Zemana AntiLogger, which you can use with certain limitations for free as long as it is for personal use according to its developer.
The tool It has a small switch that will activate or deactivate the detection function of the keyloggers, having to make use of it only when we are going to write the access credentials to a website. In the free version (and for an unlimited time) the application will prevent these keyloggers from capturing what we type in front of the keyboard and will always keep us protected only in this environment. If we have a good antivirus systemWe will absolutely not need anything else, as the rest of the functionalities in Zemana AntiLogger in the paid version will be covered perfectly well by our default antivirus.
3. Protecting ourselves from keyloggers with KeyScrambler
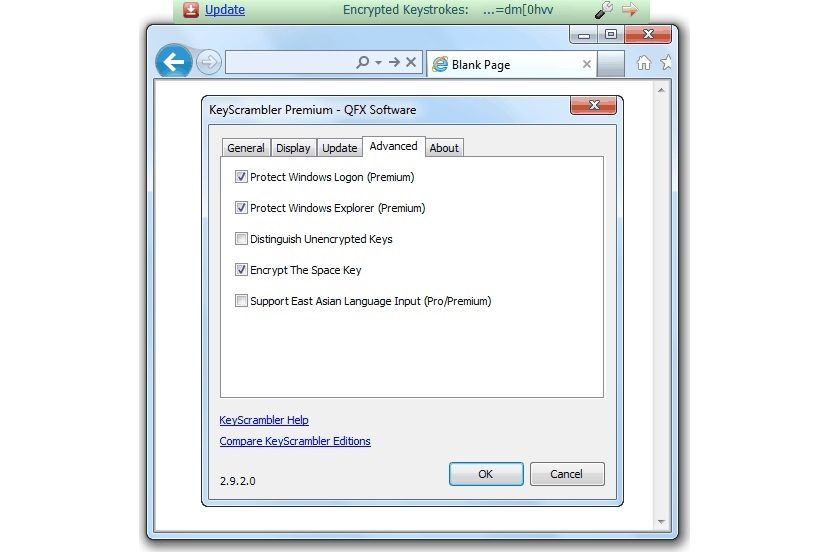
Another very interesting tool that we could be using is the one named KeyScrambler, which keeps similar characteristics when using their respective licenses. According to the developer, you can use the free version with many more functions than what other similar paid tools offer you.
When executing KeyScrambler we will go directly to the configuration area; there we will have to define what the tool should do for us, that is, the type of protection it should offer us so that keyloggers do not detect our keyboard activity.
While it is true that these applications and tools can greatly help us to avoid the presence of keyloggers, there are many other activities that we should take into account when using a personal computer that is not ours; for example, the type of antivirus that said equipment may have as well as, if the computer is for public use or belongs to a friend of ours.