The word Superfish may not be familiar to you until it has started to catch on this week. It is an adware that has harmed Lenovo users. The company has been marketing a series of computers with this adware that serves up our personal information to any hacker. It is important to know what is Superfish and how does it affect teamss that integrate this adware, since if you have a Lenovo computer with Superfish it is advisable that you eliminate the program as soon as possible.
At first, Lenovo kept silent and did not comment on this matter, despite the fact that there were dozens of tests published by its users everywhere. Finally, two days ago, several company spokespersons recognized the existence of Superfish on their teams and apologized for it. Hours later, Lenovo has released a tool that will help every user to get rid of Superfish quickly. In this guide we answer the most frequently asked questions related to Superfish and show you how to remove adware.
What is Superfish? What are your risks?
We begin this section by collecting the statements of Lenovo spokespersons. According to these official sources, «the company installed Superfish for the benefit of users, so that they could find a browsing experience with a higher level of customization«. From Lenovo they have assured that they were not aware of all the security dangers involved in using this adware. Lenovo experts only realized the dangers of Superfish once they began to disassemble it on Thursday, February 19. Superfish is an application designed to help users shop. This application injects banners and links into the navigation, something that can be extremely uncomfortable for more than one user.
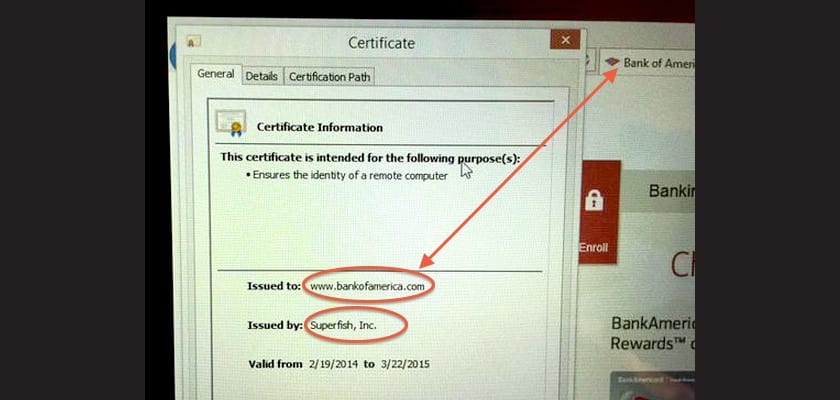
Superfish is a adware capable of installing its own security certificates, which helps you bypass some HTTPS web connection standards. The way this adware encrypts information is so weak that it leaves dozens of security holes open along the way, exposing our information. Any hacker could use these vulnerabilities to steal access data to the victims' email and they would even have the doors open to access bank accounts. At this point we can confirm that the danger of Superfish is more than evident.
One day after the scandal came to light, the United States government issued a cybersecurity statement recommending all Lenovo users to remove the adware. The Department of Homeland Security even rated this software as «spyware«.
Peter Hortensius, CTO of Lenovo, has assured that "Superfish has not been used to attack the security of users". The CTO added that “it is important to understand that not all available programs are going to be of interest to everyone. We used Superfish thinking that it would be of interest to certain people, but obviously we never came to think that it would have undesirable effects.
The next logical question would be to ask whether Superfish has come to affect users. At the moment there is no obvious evidence of this. A security expert revealed on Friday what could be done by taking advantage of these holes that the program left uncovered. However, Lenovo has not been able to guarantee, at least for now, if hackers have been making use of these security breaches.
Has Lenovo made a profit through Superfish?

The company has come under great criticism in recent hours for defending its initial position: that this application had been installed for the benefit of users, when really Lenovo would be taking a commission for each "click" or purchase of the affected users. Well, no representative of the company has wanted to confirm or deny whether, indeed, economic benefits have been obtained through the purchasing tool. Instead of giving transparent information about it, the company has chosen to sweep the other way: “We have never forced any user to install Superfish. Each one had to confirm the installation by clicking on a Yes«Peter Hortensius insisted.
What about those more inexperienced users who did not know exactly what Superfish was for or that typical user who clicks "Yes" on everything without reading things well? Lenovo's attitude seems somewhat murky in this regard and does not make things clear.
Which teams does Superfish affect?

Lenovo assured from the outset that Superfish was not installed on smartphones, tablets or equipment marketed in the business world. In the latter case, the repercussions would have been even greater, since all the confidential information of the affected companies could have been exposed to attack by any hacker.
The company has launched a complete and transparent list in which all the computers on which you installed Superfish of fabric. Here it is:
G Series: G410, G510, G710, G40-70, G50-70, G40-30, G50-30, G40-45, G50-45
U Series: U330P, U430P, U330Touch, U430Touch, U530Touch
Y Series: Y430P, Y40-70, Y50-70
Z Series: Z40-75, Z50-75, Z40-70, Z50-70
S Series: S310, S410, S40-70, S415, S415Touch, S20-30, S20-30Touch
Flex Series: Flex2 14D, Flex2 15D, Flex2 14, Flex2 15, Flex2 14 (BTM), Flex2 15 (BTM), Flex 10
MIIX Series: MIIX2-8, MIIX2-10, MIIX2-11
YOGA Series: YOGA2Pro-13, YOGA2-13, YOGA2-11BTM, YOGA2-11HSW
E Series: E10-30
Lenovo has failed to indicate the exact number of computers that could have been affected and apparently the company has no intention of making this figure public. Another way to know if your computer is "infected" is by using this test created by Filippo Valsorda, security expert.
What should I do if my computer has Superfish installed?
From Lenovo they have put the batteries in this matter. Initially, the company issued a statement giving instructions about how to uninstall Superfish manually, but he added that his team of software experts were already developing a tool that would carry out the entire process automatically.
The program to remove Superfish is now available and can be found in the Lenovo official website. Once downloaded, the tool will take care of not only remove Superfish, but it will also take care of closing all the security holes that the adware has left in our browsers.
What happens to those people who do not know everything that has happened with Superfish throughout the week? Lenovo is working together with Microsoft and McAfee so that their security tools detect adware and quarantine it. In fact, Microsoft has already updated its databases to take care of block Superfish on the affected computers. Thus, the problem will be solved practically by itself, for anyone who has not seen any information about it.
How to remove Superfish manually
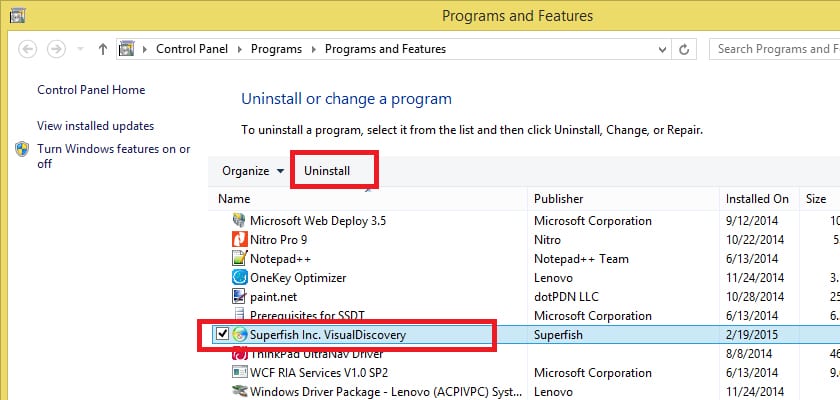
If you prefer to kill Superfish yourself, the steps to follow are simple. The first thing we will do is uninstall the program. To do this, we will go to the search option on our Windows computer and enter «Remove Programs», click on «Add or remove programs». In the list find this name: «Superfish Inc. Visual Discovery»And click on« Uninstall ».
After uninstalling the program, some of your certificates may still be stored in browsers. For remove such certificates from Internet Explorer, Google Chrome, Opera, Safari and Maxthon, open the search and enter «Certificates»: click on «Manage computer certificates». If you get a Windows security message asking if you want to authorize changes, click on "yes".
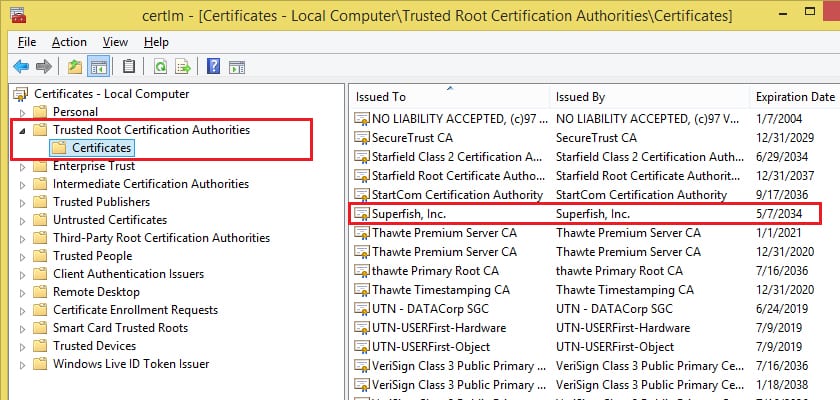
In the new window, look for the folder that says "Trusted Root Certification Authorities" and in the right part of the window look for Superfish. Click with the right mouse button and delete them.
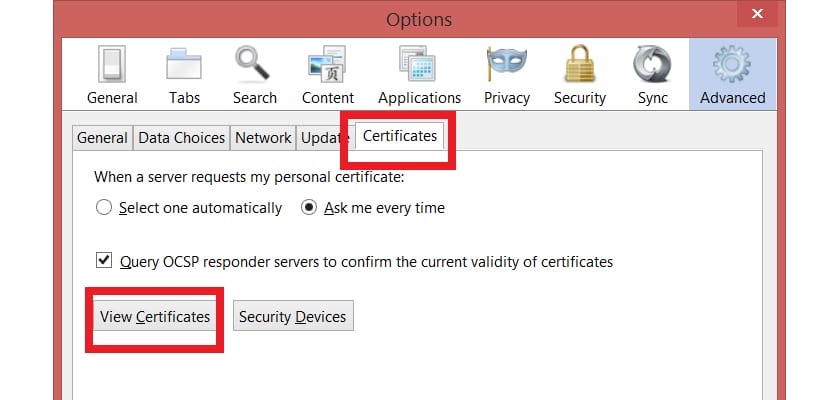
For remove certificates in firefox, access the browser settings, go to Options- Advanced. Click on the "Certificates" tab and then on "View Certificates". Under the "Authorities" section, find Superfish and manually delete all those certificates.
Your computer will have been clean.